Topic: hackers
How hackers poison your code
Hackers are always looking for new ways to compromise applications. As languages, tools and architectures evolve, so do application exploits. And the latest target is developers. Traditionally, software supply chain exploits, such as the Struts incident at Equifax, depended on an organization’s failure to patch a known vulnerability. More recently, supply chain attacks have taken … continue reading
Equifax agrees to pay at least $575 million in data breach settlement
Equifax will finally have to pay for its 2017 data breach, which compromised up to 147 million users and exposed sensitive information like credit card numbers, social security numbers, names, birthdays and addresses. The Federal Trade Commission (FTC) has revealed Equifax has agreed to pay at least $575 million as part of a global settlement … continue reading
Hackers are still sticking to the tried-and-true methods
Despite evolutions in technology, hackers are still using the same old tricks, though sometimes in a more evolved way. The hacker mentality is to want to grab the low-hanging fruit, or go after the easiest target, explained Sivan Rauscher, co-founder and CEO of SAM, a network security company. For attackers trying to find those low-hanging … continue reading
The hidden costs of data breaches
The average cost of a data breach is $3.86 million globally. That is a 6.4 percent increase from 2017, a newly released report revealed. The Cost of a Data Breach 2018 conducted by Ponemon Institute and sponsored by IBM Security found the cost of data breaches on a business’ bottom line has been steadily increasing … continue reading
SD Times news digest: Linux Foundation releases open-source jobs report, Android Studio 3.2 beta and Rust 1.27
The Linux Foundation in collaboration with Dice.com has revealed the 2018 Open Source Jobs Report. The report is designed to examine trends in open-source careers as well as find out which skills are the most in demand. Key findings included 83 percent of hiring managers believes hiring open source talet is a priority and Linux … continue reading
SD Times news digest: Amazon adds memory to Alexa, Oath pays $400,000 to hackers, Google launches new credits program for researchers, Linux Foundation welcomes 41 new members
Amazon had announced the addition of memory capabilities to its artificial intelligence, Alexa. It can remember any information for you so that you will not forget. The company also plans to add deep learning models to the spoken language understanding of Alexa. “We’ve only begun to scratch the surface of what’s possible,” said Ruhi Sarikaya … continue reading
Cyberextortion: A growing Internet problem
“If you’re gonna commit a crime,” as “Slick Willie” Sutton said when asked why he robbed banks, “That’s where the money is.” Also known as “Willie the Actor” for his ability to disguise himself, Sutton stole an estimated $2 million during his 40-year robbery career. Modern-day cyber criminals have adopted this approach to digital extortion … continue reading
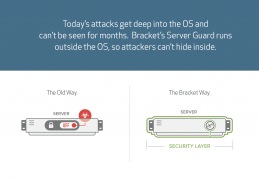
How your security budget helps hackers win
When a single breach can cause untold damage to your business, from millions in losses to reputational damage, operational disruption, and lost trust, you want to align your security budget with the actual threats you face. So why does the typical company allocate less than 3% of its security budget to application security—when a full 30% of successful breaches … continue reading
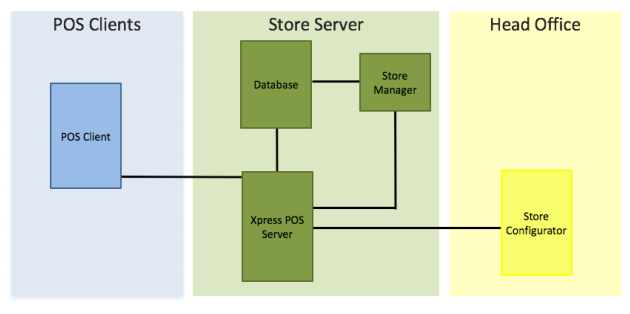
Researchers: SAP Point-of-Sale systems vulnerable to attack
There are many ways hackers can exploit vulnerabilities to get the information they want. Flaws in Point-of-Sale (PoS) systems is on this list, and ERPScan researchers recently found that PoS software distributed by German vendor SAP is missing crucial checks that leave it vulnerable to unauthorized access and modification. A video demonstration by the research team shows a … continue reading
SD Times GitHub project of the week: Awesome Hacking
When we hear the word hacker today, our minds often wander. We end up picturing a creepy person in dark clothing, in a dark room, maliciously gaining unauthorized access to systems in corporations and governments. While hacker is synonymous with “criminal” or “bad-guy/girl,” there are all kind of hackers in the hacker community. A trending GitHub … continue reading
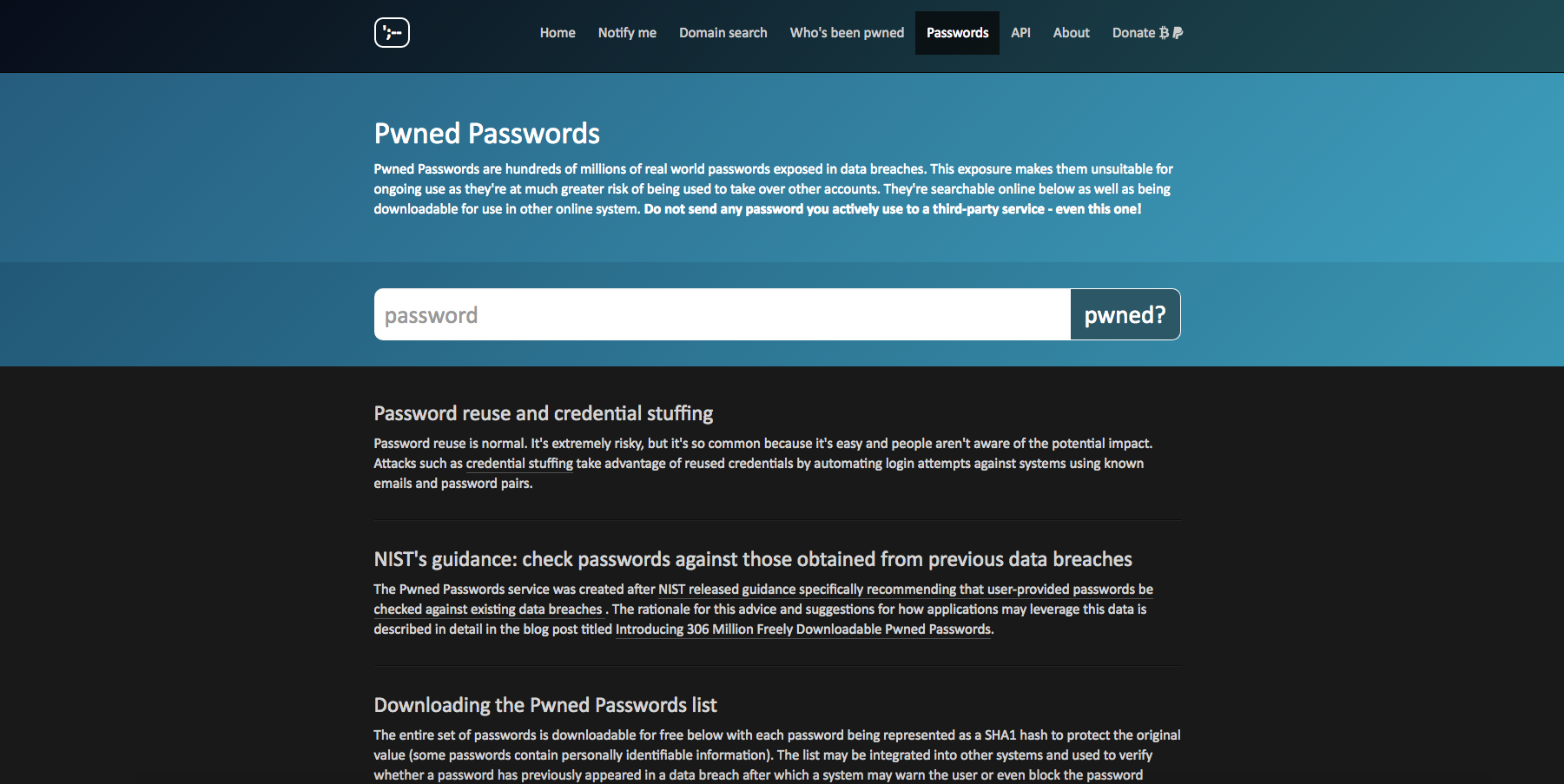
Have I been Pwned? PyTorch v0.2.0, and new vulnerability data from Netsparker — SD Times news digest: August 7, 2017
Troy Hunt, a Microsoft regional director and security guru, released 320 million freely downloadable “Pwned Passwords” to shed light on how many real-world passwords have been exposed in data breaches. The service was created after NIST released guidance recommending that user-provided passwords be checked against existing data breaches. “My hope is that an easily accessible … continue reading