Topic: supply chain
How does blockchain fit into today’s enterprise?
Web3. Cryptocurrency. Non-fungible tokens. Those are the words many think of when they hear the word blockchain. These are the areas where this emerging technology has garnered the most popularity over the years, but blockchain as a technical concept can be applied in many different ways, and it has uses in the enterprise, particularly when … continue reading
Most severe supply chain attacks occur due to third-party dependencies
Software supply chain attacks occur primarily because most software development involves using third-party dependencies. The most severe attacks occur on a “Zero Day,” which refers to vulnerabilities that have been discovered without any available patch or fix, according to William Manning, solution architect at DevOps platform provider JFrog, in an ITOps Times Live! on-demand webinar … continue reading
Sonatype’s OSS security offerings can now be deployed in the cloud
The software supply chain security company Sonatype is attempting to make it easier for development and security teams to come together and innovate. They announced new deployment options, enabling companies to run Sonatype software in the cloud. Nexus Lifecycle and Nexus Firewall can now be deployed in the cloud, which enables companies to get up … continue reading
NSA’s and CISA’s recent security guidance: The good and the bad
The NSA and CISA released the guide “Securing the Software Supply Chain: Recommended Practices Guide for Developers” last month and while David Wheeler, the director of open-source supply chain security at the Linux Foundation and OpenSS, welcomes it, he said there are some questionable requirements. The guide covers aspects of security such as how to … continue reading
Ox Security emerges from stealth with $34M to provide end-to-end software supply chain security
Tel Aviv, Israel, September 29, 2022 — Ox Security, the end-to-end software supply chain security platform for DevSecOps, exited stealth today with $34M in funding led by Evolution Equity Partners, Team8, and M12, Microsoft’s venture fund, with participation from Rain Capital. OX was founded less than a year ago by Neatsun Ziv and Lior Arzi, … continue reading
Threat landscapes: An upstream and downstream moving target
In recent years, hackers have become very sophisticated in the ways they attack upstream development pipelines by introducing vulnerabilities into the software supply chain. The popularity of open source makes those repositories a low-hanging fruit to target. In an SD Times Live! Event titled “Threat Landscapes: An Upstream and Downstream Moving Target,” Theresa Mammarella, developer … continue reading
Enterprise open source and the security of the software supply chain
In late 2021, a vulnerability was detected in the Java logging package Log4j, which is the most popular framework for logging in Java. It is used in millions of applications. Not only that, but it is used as a dependency in over 7,000 open-source projects, according to research from software security company Sonatype. Given the … continue reading
SD Times news digest: Android 12 Developer Preview 3, ComponentOne 2021 v1, and WhiteSource acquires Diffend
Google has announced the third developer preview of its upcoming 12.0 release. The latest preview includes a new app launch experience, new video and camera capabilities and new permissions for exact alarms that help users save battery. Developers can use new splash screen APIs and resources to manage the splash screen window’s background color, replace … continue reading
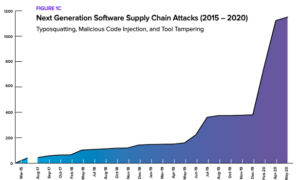
Report: A 430% increase in next-generation supply chain attacks in last year
The past year saw a 430% increase in next-generation cyber attacks aimed at actively infiltrating open source software supply chains, according to the 2020 State of the Software Supply Chain report. In the past 12 months, 929 next-generation software supply chain attacks were recorded. By comparison, 216 such attacks were recorded between February 2015 and … continue reading
Analyst View: What constraints disrupt the software supply chain?
Since COVID-19 took hold as a global pandemic, we have seen a lot of focus in the United States on improving our healthcare supply chain, by eliminating barriers to coordination among the many parties needed to source, build, transport and sell pharmaceuticals and equipment that medical professionals need. There’s no simple fix available here. Supplier … continue reading
2020 Software Supply Chain Must-Knows
Open source software is taking the world of software development into new frontiers and changing the way industries create and consume software. However, there is a learning curve with open source use and businesses need to not only be able to trust the open source software being used in their solutions, but they need to … continue reading
A managed open-source approach can improve the health of your open-source supply chain
The rise in attacks against the software supply chain is one outgrowth of vulnerabilities in open-source code that go unnoticed and therefore unpatched, a problem that has escalated despite the best efforts of enterprise development teams. As many recent high-profile breaches have underscored, it takes little for an overlooked patch to wreak havoc. Even those … continue reading