Topic: devsecops
A guide to DevSecOps offerings
Contrast Software Contrast Assess produces accurate results without dependence on application security experts, using deep security instrumentation to analyze code in real time from within the application. It scales because it instruments application security into each application, delivering vulnerability assessment across an entire application portfolio. Contrast Assess integrates seamlessly into the software lifecycle and into … continue reading
What does Contrast bring to the table and address DevSecOps in your solution?
Jeff Williams, co-founder and CTO, Contrast Security: Contrast is an integration platform for application security. We use an instrumentation-based approach, so we work from inside the running application layer. From there, we support the entire software life cycle with three things. The first thing is, we help identify vulnerabilities. Typically you want them to be … continue reading
For effective DevSecOps, shift left AND extend right
DevSecOps has come to be known by many as the shifting left of security, making it a key part of software development while code is being written, as opposed to trying to put security onto the application after it’s completed. This follows the trends of DevOps, which moved operational considerations for applications into development, as … continue reading
Shifting left for better security? It’s just as important to shift right too
There’s been a lot of talk lately in security and development circles about the need to shift left in the software development lifecycle—and rightly so. By bringing security into the picture from the beginning, you can catch weak designs and bugs earlier, when they’re cheaper and easier to fix. So far, so good. But does … continue reading
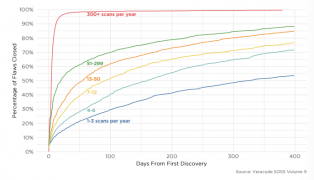
Veracode: DevSecOps is having a positive impact on security, but the state of security still has a long way to go
Even with a stronger focus on security this year, most software is still riddled with security vulnerabilities. According to Veracode’s State of Software Security (SOSS) report, 87.5 percent of Java applications, 92 percent of C++ applications, and 85.7 percent of .NET application contain at least one vulnerability. In addition, over 13 percent of applications contain … continue reading
SD Times news digest: Android Pie SDK, Contrast Security’s free DevSecOps solution, and Status partners with Nim
Following this week’s announcement of Android 9 Pie, Google is releasing a new Android SDK that offers more Kotlin features. According to the company, Android developers often run into problems with the Java programming language when accessing a null reference. Kotlin addresses this problem by providing nullable and non-nullable types in the type system, the … continue reading
A guide to DevSecOps tools
Aqua Security enables enterprises to secure their container and cloud-native applications from development to production, accelerating application deployment and bridging the gap between DevOps and IT security. The Aqua Container Security Platform protects applications running on-premises or in the cloud, across a broad range of platform technologies, orchestrators and cloud providers. Aqua secures the entire … continue reading
How these companies can help make your applications more secure
Dror Davidoff, co-founder and CEO of Aqua Security Aqua Security enables enterprises to secure their container-based and cloud-native applications from development to production, accelerating container adoption and bridging the gap between DevOps and IT security. Images serve as a container’s foundation, and developers can easily pull them from a centralized registry to run containers in … continue reading
Application security needs to shift left
As teams are pressured to release software more rapidly, more and more aspects of software development are being forced to “shift left,” moving up earlier in the development lifecycle. Because of the speed in which code is updated and delivered, security can no longer be thought of as an afterthought, said Rani Osnat, VP of … continue reading
What does it take to build a secure app by design?
We are entering a new stage of app development. While, until now, requirements for architecture were left to the discretion of companies, developers and their target audiences, recent legal changes in the European Union and the United States have brought a new player to the table: regulations. Most notably, the EU’s General Data Protection Regulation … continue reading
JFrog Xray 2.0 examines the CI/CD pipeline
JFrog has announced the latest release of its continuous security and universal artifact analysis solution. JFrog Xray 2.0 is designed to give DevOps teams insight into potential problems and the confidence to release into development, deployment and production stages. “Developers are incorporating an ever-growing number of artifacts from external and internal sources into their … continue reading
CA Technologies acquires SourceClear for its DevSecOps portfolio
CA Technologies announced its acquisition of software composition analysis specialists SourceClear early this week with aims to incorporate SourceClear’s SaaS-based SCA tool and proprietary vulnerability database with their Veracode cloud platform. “We are excited about what this acquisition means for our customers in terms of increased support for SCA in DevSecOps environments and the ability … continue reading