Topic: owasp
How policy-as-code can simplify API security
Most organizations today use hundreds of applications in their environment, and with that they employ hundreds of APIs to connect these to the necessary web servers. Due to the flow of sensitive information, it’s crucial to manage policies that ensure controls are in place to only authorize appropriate access, as well as actions that can … continue reading
2021 Year in Review: Security
2021 was a tumultuous time for security, marking both massive breaches — a trend that sped up during the pandemic — and widespread action for trying to fix the problem. On May 7, 2021, the Colonial Pipeline, an American oil pipeline system, suffered a ransomware cyberattack that impacted computerized equipment managing the pipeline. In response, … continue reading
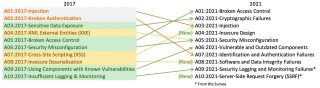
Broken Access Control is now the highest vulnerability in OWASP Top 10 2021
The latest edition of the OWASP Top 10 showed that all of the highest-priority vulnerabilities since 2017 have shifted and new ones have been introduced. Broken Access Control has dethroned Injection as the top vulnerability, whereas it previously held fifth place. The 34 Common Weakness Enumerations (CWEs) mapped to Broken Access Control had more occurrences … continue reading
SD Times Open-Source Project of the Week: OWASP SAMM
The Open Web Application Security Project (OWASP) has announced version 2 of the Software Assurance Maturity Model (SAMM). SAMM is an open-source framework that enables teams and developers to assess, formulate and implement better security strategies that can be integrated into the software development life cycle. “Our mission is to provide an effective and measurable … continue reading
‘Security debt’ focus of 2019 State of Software Security report
In 2011, Marc Andreessen wrote an article in the Wall Street Journal that included the now-famous phrase “software is eating the world.” Eight years on, that statement rings truer than ever. It’s not a stretch to say that software is eating the cybersecurity world as well. The fallout from not integrating security early in the … continue reading
HackerOne: The top 10 security vulnerabilities
Companies are paying the highest amount of bounties to fix cross-site scripting (XSS), improper authentication and information disclosure vulnerabilities. Meanwhile, some cloud-based vulnerabilities such as server-side request forgery (SSRF), in which an attacker can abuse functionality on the server to read or update internal resources, are seeing an uptick in bounties. This is according to … continue reading
For effective DevSecOps, shift left AND extend right
DevSecOps has come to be known by many as the shifting left of security, making it a key part of software development while code is being written, as opposed to trying to put security onto the application after it’s completed. This follows the trends of DevOps, which moved operational considerations for applications into development, as … continue reading
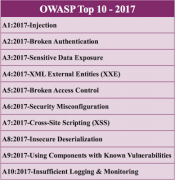
OWASP releases the Top 10 2017 security risks
The Open Web Application Security Project (OWASP) officially released its Top 10 most critical web application security risks. This is the first time the organization has updated the Top 10 since 2013. “Change has accelerated over the last four years, and the OWASP Top 10 needed to change. We’ve completely refactored the OWASP Top 10, … continue reading
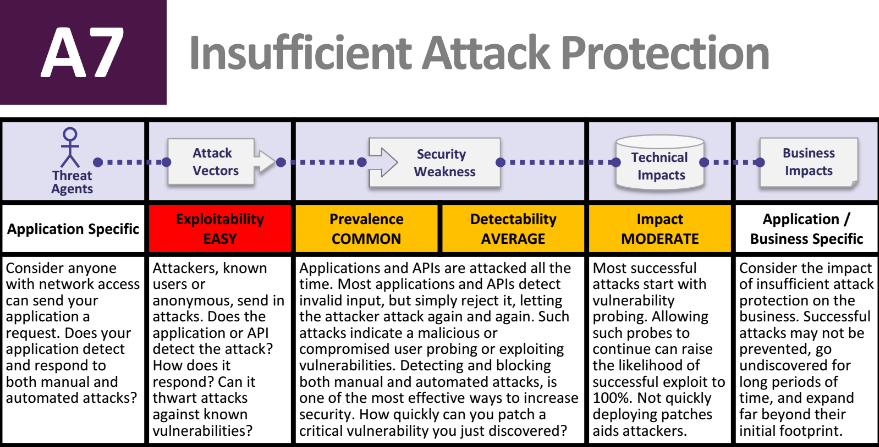
Synopsys calls for removal, replacement of OWASP Top 10-A7
This year, the Open Web Application Security Project (OWASP) released its Top 10 2017 project for public review. There were two vulnerability updates to this year’s 14th release of OWASP, and although they were added to raise awareness on security risks in applications, one company is calling a movement for removal and replacement of one … continue reading
Signal Sciences releases new web protection platform
Signal Sciences today announced the availability of its Signal Sciences Web Protection Platform (WPP). WPP is new platform designed to provide threat protection for web applications, APIs, and microservices on any platform. This platform launch comes on the heels of Signal Sciences’ announcement of a $15 million series B funding round led by CRV. Signal … continue reading
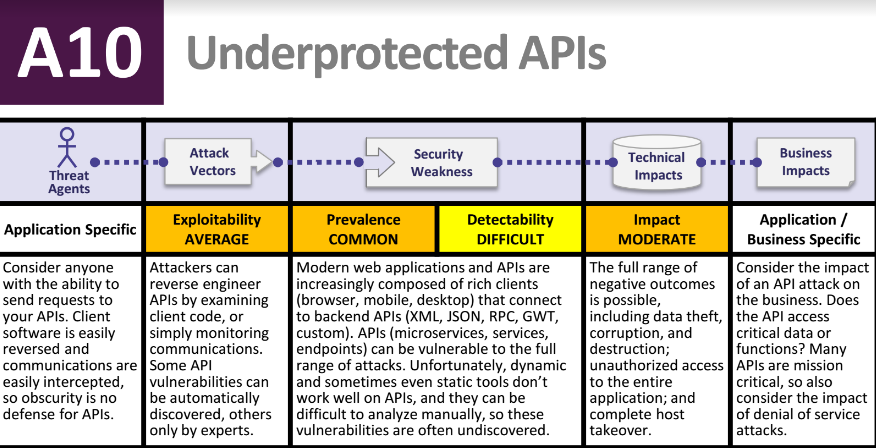
OWASP adds unprotected APIs, insufficient attack protection to Top Ten 2017 release
The Open Web Application Security Project (OWASP) released its Top 10 2017 project for public comment. This is the 14th year OWASP is raising awareness of security risks with its list, and it contains two major vulnerability updates, example attack scenarios, and a list of free and open resources for security-conscious developers. When Jeff Williams, OWASP … continue reading
RSA Conference goes smaller, focuses more on timeless problems
The software security world is prone to ebbing and flowing. Twenty years ago, firewalls were the new hot solution. Fifteen years later, there were these hot new things called application firewalls. What was old was new again. So it was at the annual RSA Conference this year. Last year was something of a flush out, … continue reading