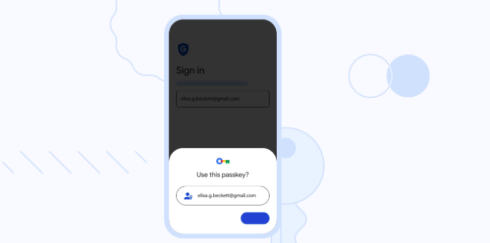
Last year, Google announced it was starting to work on adding support for passkeys, which is an authentication method that allows users to sign in with a fingerprint, facial recognition, or PIN code, similar to how you unlock your phone.
Today the company is announcing that passkeys can now be used to sign into your Google Account.
“Using passwords puts a lot of responsibility on users. Choosing strong passwords and remembering them across various accounts can be hard. In addition, even the most savvy users are often misled into giving them up during phishing attempts. 2SV (2FA/MFA) helps, but again puts strain on the user with additional, unwanted friction and still doesn’t fully protect against phishing attacks and targeted attacks like “SIM swaps” for SMS verification. Passkeys help address all these issues,” Arnar Birgisson, software engineer at Google, and Diana K Smetters, principal engineer at Google, wrote in a blog post.
When you add a passkey to your Google Account, it is stored locally on your device. This means that passkeys cannot be shared or written down like a password, so they are less prone to phishing attempts or ending up in the wrong hands.
Because of their strong security, Google allows you to also skip two-factor authentication when using them.
While passkeys are stored locally, this doesn’t mean you can only sign in from that one device. Each new device you enroll will have its own passkey.
You can also sync passkeys in your own backup service if you desire. For example, you can create a passkey on your iPhone and back up the key in your iCloud account, and it will be available on all your Apple devices signed into that iCloud account. This makes it less likely that you are locked out of your account when you lose your device. The company advises against doing this on devices that are shared with other people as they would also gain access to your passkey.
“While that might sound a bit alarming, most people will find it easier to control access to their devices rather than maintaining good security posture with passwords and having to be on constant lookout for phishing attempts,” Birgisson and Smetters wrote.